Audit-compliant documentation and identification services available as individual components or complete packages
Trust Center Infrastructure
for TSPs

Get certified as a TSP yourself
Audit-compliant documentations
You’re in search of a provider who can provide all the necessary documentation for the components required for certification.
Identification Services
We have a wide range of already integrated eIDAS-compliant identity verification methods.
These can be used upon request and supplemented as needed.
As individual components or complete package
Get a comprehensive plug-and-play solution or only the components you need – you decide!
Get in touch now and become a TSP with our support!
How can I become a TSP myself using SIGN8?

This speaks for SIGN8
Infrastructure components as required
SIGN8 can support you with all the necessary infrastructure components for your certification. Since we are certified as a TSP ourselves, we can optimally accompany and support you on your journey!
Made and certified in Germany
Developed by German experts, certified and monitored by the Federal Network Agency.
Safety
Our systems are checked at regular intervals in internal and external independent audits, including by the Federal Network Agency. This guarantees that we provide you with Trust Center infrastructure components of the highest quality.
Certified
SIGN8 is a certified Trust Service Provider itself. We can provide you with these Trust Centre infrastructure components as a service provider.
Can be integrated
With our deep technical expertise, we’re here to assist you in seamlessly integrating them into your systems.
Flexibility
Adapt SIGN8 to your needs. With the whitelabelling option, you can adapt the solution to your corporate design.
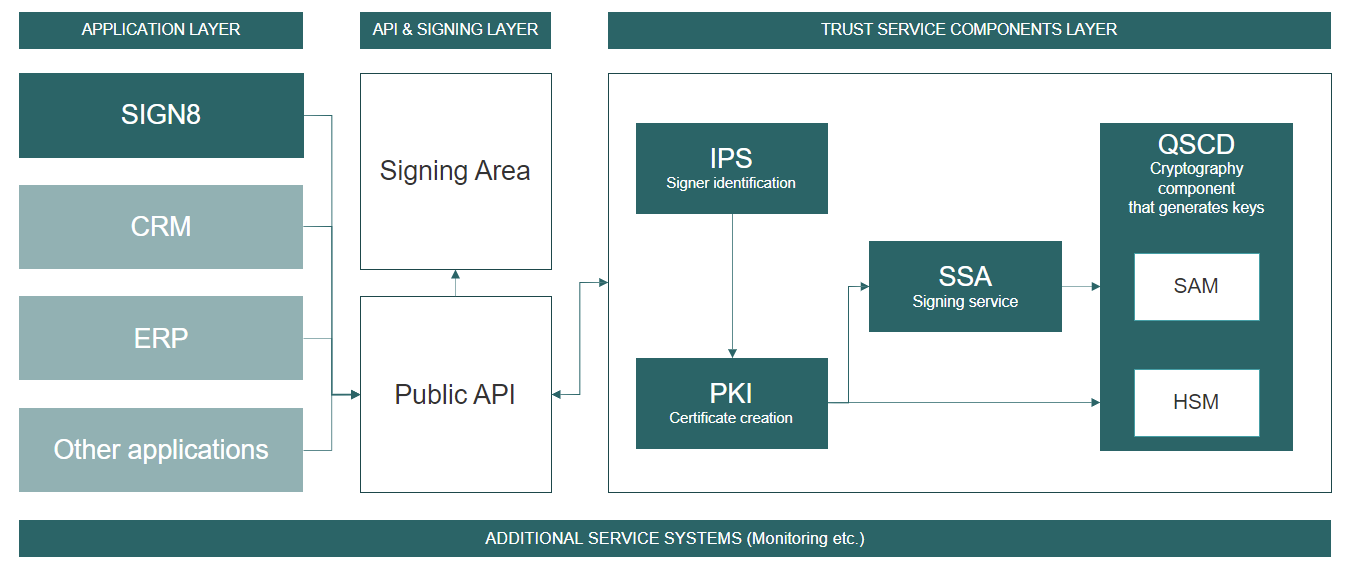
Trust Centre Infrastructure Technology for TSPs
The diagram illustrates the individual and scalable components of the Trust Center infrastructure from a technological perspective. The interaction of the elements in the different layers is of particular importance. The delivery of the individual components takes place on a modern, agile, scalable container architecture.
Glossary
QSCD
A QSCD (Qualified Secure Creation Device) is the combination of HSM and SAM.
SAM
A SAM (Secure Access Module) is the software module for communication and control of the HSM. The SAM takes over the key management and is addressed by the PKI.
SIC
The SIC (Signing Interaction Component) is used for the interaction of the signer with the signature workflow. The signer is presented with the workflow, can review their data, inspect the document, make inputs, and then proceed to identify or authenticate themselves in order to sign.
SIPO
A SIPO (Signature Portal) is the platform for creating, requesting and executing signatures within the framework of individual workflows.
IPS
The IPS (Identity Provider Service) is a component that is responsible for the identification and authentication of the signer. To accomplish this, the component sends OTPs, communicates with identity providers, and validates the results against the respective signing requests.
HSM
An HSM (Hardware Security Module) is a hardware module for the secure and efficient execution of cryptographic operations or applications. For example, it generates the key pair needed for the signature.
OCSP
An OCSP (Online Certificate Status Protocol) is a network protocol that allows users to query the status of a certificate with our validation service. The OCSP is used by PDF readers to validate whether a signature is valid.
PKI
A PKI (Public Key Infrastructure) is a collection of technologies, policies and procedures used to manage public keys, digital certificates and trust relationships.
SSA
The SSA (Signing Service Application) receives the data to be signed and the signer’s private key, creates the signature from it and links it to, for example, the PaDES standard for PDFs. For this purpose, the Long-Term Validation (LTV) concept is used, allowing the signatures to be verified far into the future.
Start the first steps
Needs analysis
As a first step, we will conduct a needs analysis together with you to precisely understand how your path to becoming a TSP looks in detail.
We accompany you, according to your preference, collaboratively throughout the entire journey or only during specific stages.
Contract and provision of services and infrastructure
Once the needs analysis has been successfully completed, the second step is to finalize the contracts in order to provide you with the required infrastructure and the desired services.
Professional Services
We will take care of all commissioned infrastructure components and services on your way to becoming a certified TSP.
Operation and maintenance
During operation, we take care of system maintenance and ensure the smooth operation of the Trust Center infrastructure.
Support
We manage the operation of the infrastructure we provide and offer you support to quickly assist with any questions or issues.

