Made with ❤️ in Munich

Digital Signatures & Seals
Manage Digital Certificates Yourself
Our Trust Center Infrastructure (TCI) allows you to manage digital certificates in a secure and high-performing on-premises server environment.
The basic functions are the legally compliant digital signing and sealing of documents. Furthermore, you have the flexibility to expand the TCI to include PKI and EUDI Wallet functions.










Everything You Need to Know About TCI

eIDAS Certified
Our solution is eIDAS-certified: for Qualified Electronic Signatures (QES) and Seals that are legally binding and recognized throughout Europe.

Flexibly Scalable
While the Trust Center Infrastructure’s basic functions are digital signing and sealing, you can also expand it to include EUDI Wallet, S/MIME, and BYOK features.
High Signature Volumes
You use a high-performance server specifically optimized for high signature volumes. It can be hosted either in your own data center or in our data center.

Highest Level of Security
Digitale Zertifikate kannst in deiner eigenen Serverumgebung verwalten – für maximale Kontrolle und höchste Sicherheit.
Onboarding Your Employees
Popular Use Case for the TCI
First, we provide you with the necessary TSP infrastructure, i.e. a server with qualified QSCD. This infrastructure is provided either as a complete package or in individual components, depending on your needs. This allows you to host digital certificates (FES, QES) directly on your premises and use them with your own signature software.
As soon as a new employee needs a digital certificate, it is requested via an API. The employee is identified and the appropriate certificate is delivered directly to the QSCD. The employee can then sign digitally immediately – securely, quickly and completely locally.
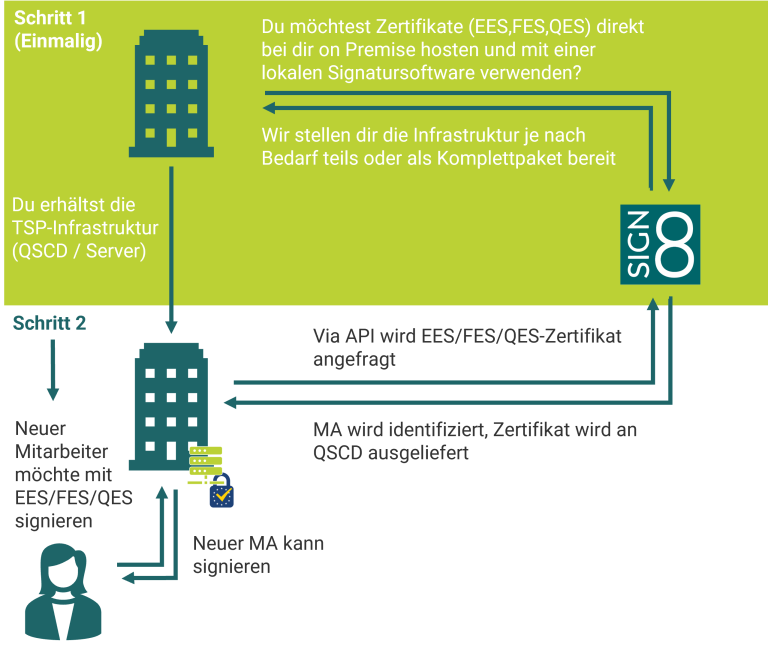
Get full control over digital certificates directly in the data centre
The Technology Behind TCI
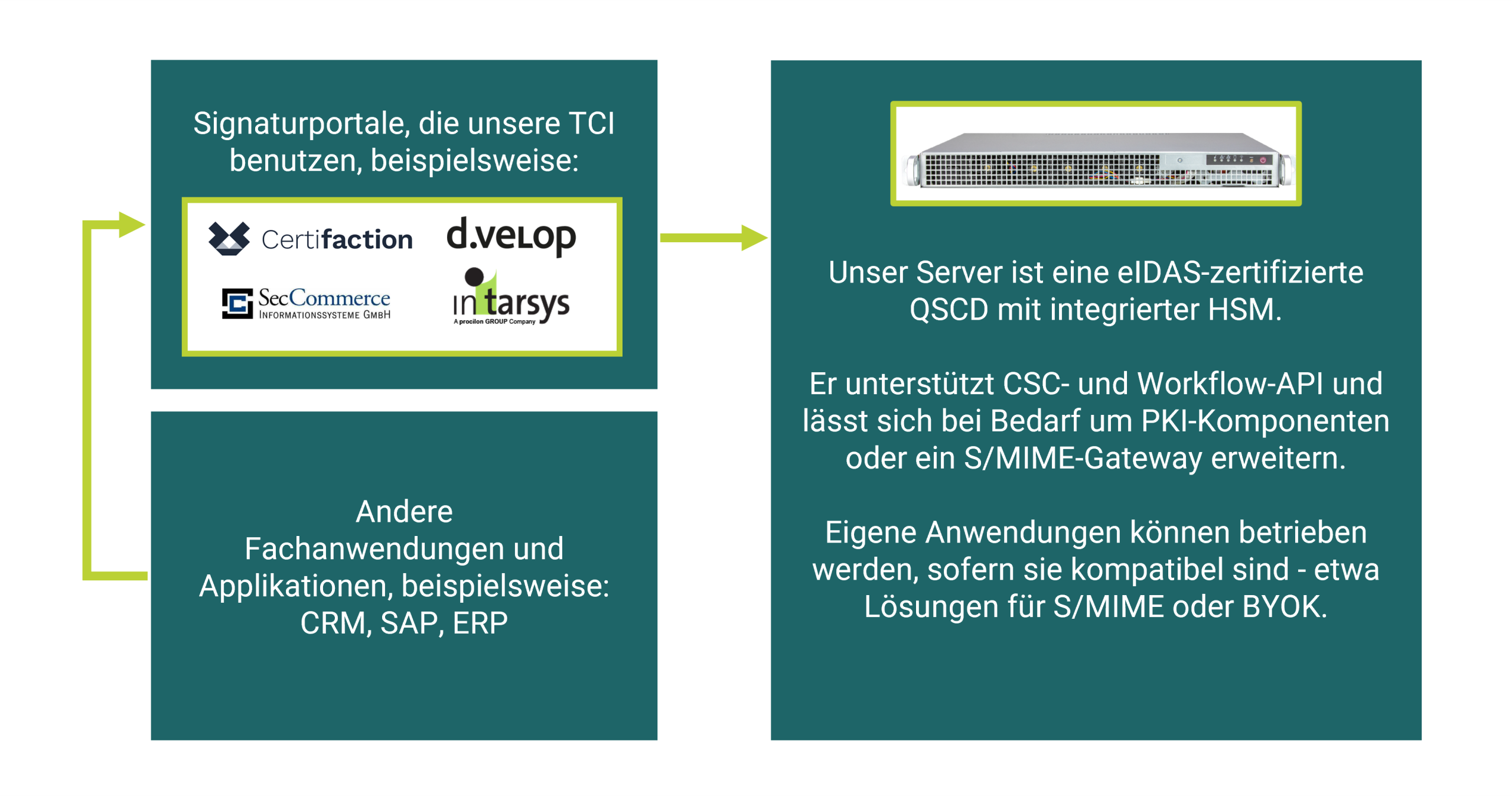
Discover optional PKI extensions for your TCI
S/MIME
To secure your email communication
With S/MIME (Secure/Multipurpose Internet Mail Extensions), you can encrypt emails and apply a digital signature. This ensures that your messages remain confidential and that recipients can clearly verify your identity.
With our TCI, you can set up S/MIME centrally without any configuration on individual devices. Simply route your email traffic through a mail gateway that automatically encrypts and signs messages for all employees.
Du musst digitale Zertifikate nicht manuell verteilen oder konfigurieren. Stattdessen behältst du die volle Kontrolle über die Sicherheit deiner Kommunikation.


Encryption
To protect your data
Whether it’s sensitive project files, internal folder structures, or entire databases – the best way to protect your data is right where it’s created.
Don’t want to compromise when using cloud services? Then simply encrypt your applications with your own keys (BYOK).
This way, you maintain full control across all storage locations both on-premises and in the cloud. Our TCI provides the infrastructure you need: centrally managed, highly secure, and tailored to your IT landscape.
Applications for PKI-Based Features
Two common encryption use cases from real-world enterprise environments
Securing your SQL database
Do you operate a Microsoft SQL database with sensitive content? Then the best way to protect your data is directly at the database level using strong encryption with your own keys. This ensures that unauthorised persons cannot access the data, either for reading or writing, even if they have physical access to the system.
Our Trust Centre Infrastructure (TCI) provides you with central key management, allowing you to control access at all times and secure it in a verifiable manner.
BYOK for Microsoft Azure & Amazon AWS
Do you use cloud services such as Microsoft Azure or Amazon Web Services but still want to retain full control over your data? With ‘Bring Your Own Key’ (BYOK), you can integrate your own encryption keys directly into cloud applications and decide for yourself who can access which data and when.
Our TCI offers you the right key provisioning and management: compatible with leading cloud platforms and 100% eIDAS-compliant.

The Benefits We Offer You
Think Speedboat – Not Ocean Liner
Small enough to stay agile. Big enough to deliver.
Got new requirements? We’ll handle it.
100% Self-Made
Our technology is 100% built in-house. No patchwork. No third-party dependencies. Just complete control and total flexibility.
Real People. Not Anonymous Systems.
No bots call you back here. We talk to you as equals and truly listen – even beyond business topics.
Buddy Vibes
We know each other, value each other, and sometimes just pick up the phone for a quick chat.
